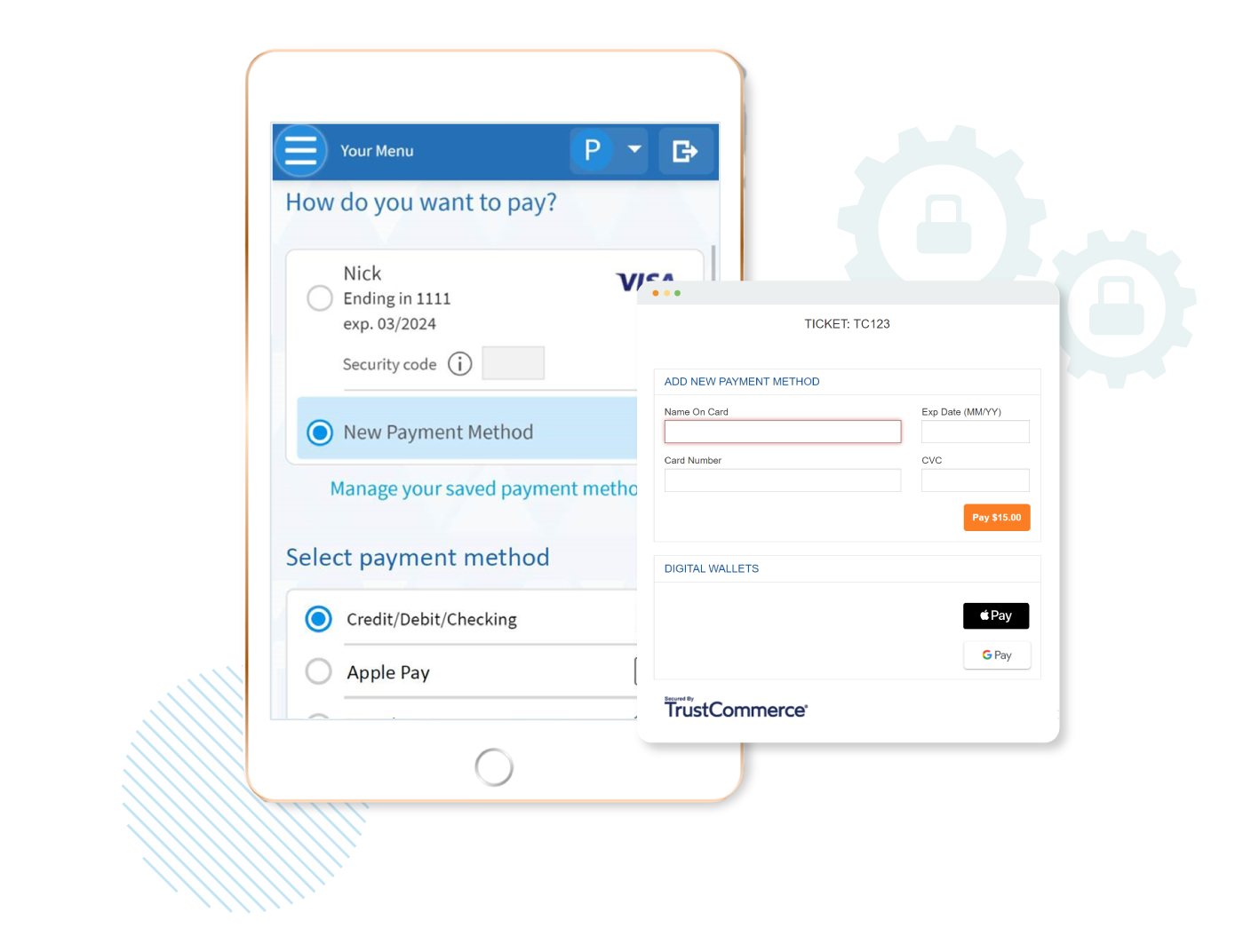
TrustCommerce Announces Cloud Payments Integration with Practice Fusion
TrustCommerce’s Cloud Payments platform is now integrated with Practice Fusion, a Veradigm Network solution. Healthcare providers are able to collect payments from patients directly within